24 Sep, 2019

Phishing attacks have become a widespread issue for most of individuals and organizations. According to an Accenture report, 85% of businesses face phishing and social engineering attacks, up 16% from the last year.
Another research by Avanan found that 1 out of 25 business emails are phishing emails and more than 50% of them contain malware. Needless to say, phishing attacks are on the rise and it’s time for us to become aware and have some phishing protection practices in place.
If you are wondering what are two ways to protect yourself from phishing scams, then this article is for you. In fact, we have covered more than two ways. Before diving into the ways to protect, let’s us first discuss what it is.
A phishing attack is a new kind of cyber attack that is carried out using fraud email messages. These emails look safe and from a trusted person or company but contain malicious links and attachments. Once clicked, these malicious things have the power to collect your confidential information from the system and send it to the attackers.
1. Keep yourself informed
Cybercriminals are creating new types of phishing scams every day. It’s crucial to keep yourself updated about the new techniques used by them to avoid becoming their prey.
If you know about what attackers are up to, there are more chances to reduce the risk. IT managers in the organizations should train and inform all the employees about the new phishing techniques used by attackers, along with the ways to protect against them.
2. Be smart while opening emails
While opening the unknown emails and browsing social media, be sensible and smart. You should not click on the links in emails without knowing their destination. Sometimes, the emails might look from a reliable source, but the destination of the links can be dangerous. By placing the cursor on the link, check whether the link on the text and the link appearing for mouse-hover are same.
What you should also do is copy the link and paste it into your browser. Now check if the link in the email and the browser are same. Avoid or delete emails that ask for sensitive information like contact info or banking details. Banks and other trusted organizations don’t ask for such information on emails.
3. Beware of shortened links
Companies and individuals make use of shortened URLs with the help of platforms like Bitly and TinyURL. While the shortened links help them to track the number of clicks, use more characters on Twitter, promote more sharing, and gain other benefits.
However, such links hide the destination where the user will be taken. And the attackers are using this fact for their benefits. What they are doing is using these platforms to trick users into believing that they will be taken to a trusted URL. But the truth is different. They are taken to a fake and malicious site.
Attackers can take you to dangerous websites which can steal your data, carry out a cyber attack, and inject the malware into your system. Hence, it is better to avoid the shortened links if they are from an unknown source.
4. Use anti-phishing toolbars
Anti-phishing toolbars used in your browser can significantly reduce the risks of visiting malicious websites. After copying the link from your emails, paste it into the toolbar. If it is a malicious link, the toolbar will warn you to not visit it.
These toolbars can work as an additional security layer for your system and help you protect against dangerous websites. These toolbars are available for free and are a must-have thing nowadays.
If you are not sure which toolbar is right for you, we are here to help. These are the top anti-phishing toolbars available at no cost—
5. Read the emails carefully
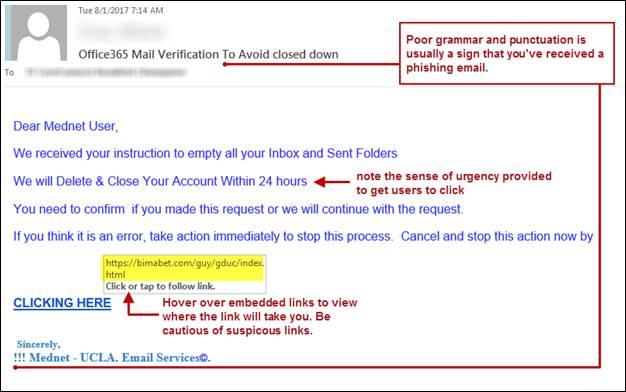
For most of the emails, you can find whether it is dangerous or not, just by reading it carefully. Most of the times, such mails have some typos, exclamation marks, capital letters randomly, poor grammar or similar domain name in the email address.
For example, the attackers use similar domain names and email addresses such as [email protected]. You might think it is from Amazon and follow things mentioned in the email, which might result in a successful attack.
They also try to keep a sense of urgency to drive the click rate on malicious links. They will try to scare you by saying that your services will expire within a day, or your account will be closed in a few hours if you don’t proceed further by clicking the links in the email.
Plus, attackers also use big occasions like festivals to send emails offering free vouchers, high discounts etc, which is a great way for them to carry out attacks. Hence, read the emails carefully.
6. Check for SSL certificate
SSL certificates are the new norm for all the websites nowadays. Whenever you open a website, check whether the URL is beginning with HTTP or HTTPS. The ‘S’ in the HTTPS indicates that the website is secure and your connection with the site is encrypted.
This is all the more crucial when you submit your personal information or banking details to make a purchase or for a subscription. Websites without SSL certificates are not secure and can allow hackers to read your details.
7. Update email passwords regularly
An email account is generally used to create other accounts as well, like Facebook, Instagram, Twitter, etc. It is used for your banking also. If it gets hacked, it can lead to the hack of other accounts as well. Furthermore, your account can be used to carry out attacks on accounts of your friends and acquaintances.
Hence, it is recommended to use strong passwords (containing a mix of characters, symbols, and numbers), and keep updating them on a monthly basis.
Wrapping up
These are a few of the best practices that you must follow to protect yourself from phishing attacks. Ensure that you check the domain of the email sender, proofread the mail if it requires link clicks, copy-paste the URL in the browser before making the final call.
If you want to get protected from intruders to check your photos, video, and notes then you can use the private gallery app to hide personal data inside your mobile phone.
 3559
3559 By Goldy Benedict
By Goldy Benedict  By Goldy Benedict
By Goldy Benedict